Skyhigh Security Cloud 6.7.0 Release Notes (June 2024)
Legends Used
|
General Availability |
IMPORTANT: The Skyhigh Security Cloud 6.7.0 release addresses significant library updates for enhancing security and stability. For additional information about these fixes and updates, contact Skyhigh Support.
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention (DLP)
User Risk Enhancements in DLP 
User Risk-Based Sanctioned DLP Policy
User risk rule is a new sanctioned DLP policy rule on the Rules & Exceptions page (found under Policy > DLP Policies > DLP Policies > Actions > Sanctioned Policy > Create New Policy > Description > Rules & Exceptions) of the sanctioned DLP policy wizard. This rule enables you to define DLP policies based on the risk types of users identified in sanctioned cloud services, ensuring stricter controls on access to sensitive data for risky users.
You can define DLP policies by configuring the rule with the available risk parameters such as low, medium, and high-risk users. The risk type of a user is determined by their current user risk score for sanctioned DLP incidents and it is rated on a scale of Low (1-3), Medium (4-6), and High-risk (7-9) types. User Risk rule allows you to apply the necessary controls to mitigate potential threats in your organization and protect your most sensitive information even from low-risk users. For details, see User Risk Rules.

View User Risk Score for Sanctioned DLP Incidents
You can now easily view the user risk score of a user on the Sanctioned DLP Incident cloud card (found under Incidents > Policy Incidents > Policy Incidents page). The sanctioned DLP incident cloud card also includes the last updated date of the risk score and the user name, in addition to the user risk score, to provide a comprehensive view of the user's risk profile. The user risk score is a near real-time dynamic risk score assigned to the user whenever the incident is updated, and it is rated on a scale of 1–9. This score is measured based on various factors such as the severity of the violation, the user’s security posture, and metadata about the user's overall compliance history. The score identifies the deviations as High (7-9), Medium (4-6), and Low-risk (1-3) types.
The user risk score allows you to track and manage user’s typical usage patterns related to data security and take necessary actions to strengthen the defense against potential threats in your organization. The Security Operations Center (SOC) can gain unified visibility of the user risk score within Incident Management workflows to efficiently categorize users based on their risk types. This enables SOCs to investigate incidents and outline remediations quickly, thereby enhancing the ability to secure their most sensitive data from risky users. For details, see View User Risk Score for Sanctioned DLP Incidents.

Historical User Risk Score Included in Incidents API
Historical User Risk Score is now included as part of the information field in the external query Incident API. As a result, DLP SOC admins can retrieve historical user risk scores and apply remediation actions quickly and efficiently. SOC admins can also use the Incidents API to import historical user risk scores into their SIEM tools. This enables them to monitor historical user risk scores for risky users within their organization. This enhancement improves operational efficiency, reduces response time, and ensures incidents are resolved promptly. Consequently, the risk of data breaches is reduced, and the impact on the organization is minimized. For details, see Incidents API Definitions.

Data Classification Enhancements 
Enhanced Proximity Classification with Unique Match Filtering
The Proximity classification is enhanced with a new option called Count each match string only one time. You can enable or disable this option to determine whether to count each matching string only once or multiple times in your Proximity classification. Activating this checkbox eliminates the duplicate match counts during the DLP Policy evaluation.
To access the new option on Proximity Classification, go to Policy > DLP Policies > Classification > Condition > Proximity. For details, see Create a Classification using Proximity.

Enhanced Keyword Rule Criteria in Classification
The criteria for classification-based keyword rule is now enhanced with new AND (is all of) and NOT (is none of) operators, in addition to the existing OR (is one of) operator. This enhancement enables you to create several complex rules for identifying sensitive data based on various conditions. Additionally, you can define multiple keyword rule criteria for a classification. Organizations can leverage the enhanced keyword rule criteria in their classifications to gain greater flexibility and granular control via DLP policies. You can find the Keyword Rule by navigating to DLP Policies > Classifications > Create/Edit Classification > Conditions > Select Criteria > Keywords. For details, see Create a Classification using Keywords.

Improved Word Boundary Scanning for Special Characters in Sanctioned DLP
Skyhigh has enhanced its ability to detect word boundaries for dictionaries configured using the Starts with and Ends with advanced settings in Sanctioned DLP. This enhancement enables Skyhigh to scan content with special characters and trigger classifications accurately. Skyhigh has updated its detection logic to the Enhanced EDM word boundary detection logic (similar to perl \b behavior) instead of the former Trellix DLP word boundary detection logic.
This improved functionality applies to data with special characters such as the em space (u+2003) in sanctioned SaaS chat applications. When Skyhigh detects these data types, it classifies the content based on the defined dictionaries, regardless of the presence of special characters.
For example, some chat applications such as Microsoft Teams, may replace tabs with em spaces in chat messages. Previously, a dictionary configured to match word boundaries might not have triggered on such content with special characters. With this enhancement (available in SSE 6.7.0 onwards), Skyhigh can precisely detect and classify such data with special characters.
Enhanced Content Detection and Extraction Libraries
Skyhigh has upgraded its content detection and extraction libraries to enhance security and stability.
Note: You must download and install the latest DLP Integrator software (v6.7.0 or later) and use the IDMTrain tool to retrain your Enhanced Index Document Matching (IDM) databases. For details, see Download the DLP Integrator.
Classification Tester for DLP Classifications 
- The Classifications page (found under Policy > DLP Policies > Classifications > Test Classification) now includes a Classification Tester available for DLP classifications.

- It generates match results for Skyhigh Built-In and Custom classifications defined using various conditions.

- The classification tester simplifies the process of validating expected match results by providing the following benefits. For details, see Evaluate Classifications.
| Classification Tester Benefits |
|---|
| Streamlined DLP Policy Deployment. Test classifications before integration in DLP policies to ensure seamless migration from data identifiers to data classification workflows. |
| Rapid Classification Validation. Quickly test classifications by entering text values or uploading files. |
| Enhanced Confidence. Test classifications independently to verify the accuracy of your DLP classifications, building trust in your DLP strategy. |
| Unified Compatibility. Supports classifications for all types of DLP policies across Skyhigh SSE (Sanctioned DLP, Shadow/Web DLP, Private Access DLP, and more). |
| Risk Reduction. Minimize the risk of inaccurate matches, preventing false positives. |
Skyhigh SSE Products
Skyhigh Secure Web Gateway
Policy Insights via Rule Tracing 
Rule tracing helps the administrators identify the policies assessed to determine whether to allow or block a request from an end user. This entire process involves 3 simple steps. The administrator would be able to initiate a unique URL using the user name and smartmatch filter parameters, which would be shared with the end user. The end user should be able to enter that URL in the browser. The administrator would initiate the trace, and view the rules evaluated for end user-generated traffic in the SSE console. Using this feature, you can clearly understand why an end-user request was allowed or denied. Contact Skyhigh Support for more information.

Enable Dashboard Notifications for Fallback Policies 
A fallback policy is triggered when there is any corruption in the configuration or if any incorrect configuration is added. With this feature, you will be able to configure and receive dashboard alerts when your configuration falls back to the default policy. You need to enable the request notification option under Analytics > Web > Web Traffic. These alerts will be available in the SSE console. For details, see Enable Dashboard Notifications for Fallback Policies.
Support for Dedicated Egress IP 
The Dedicated Egress IP feature allows you to use a dedicated IP address exclusively assigned to you for egress from SSE (Web) to the Internet. You can utilize this IP for either selected traffic or all traffic, depending on your requirements. As part of this feature, you will have the flexibility to choose the country through which you want to route your traffic. This is a feature-controlled enhancement. Contact Skyhigh Support for more information.


Selecting Languages When Cloning a Template with Multiple Languages 
When cloning a template for an End User Notification Page that has multiple languages configured, you can select the languages you want to keep for the cloned template.
You can clone a template on the End User Notification Pages page.
For example, you are going to clone a template that has English and German configured as localized templates.

You can deselect German and then clone the template.

The cloned template will only have English configured as a localized template.
Configuring the Position of the Button on an End User Notification Page 
When configuring a template for an End User Notification Page, you can configure the position of the button that allows the end user to go to a particular destination.
The button can be placed above or below the variables that are shown on this page.
You can configure a template on the End User Notification Pages page. Configuring the position of the button is one of the options that are available when configuring the Button element of a template.
For example, you can have a Contact us button on an End User Notification Page that the end user can click to be directed to a destination within your organization.
You can leave the default setting, which lets this button appear below the variables on the page.

You can also enable the Place button above variables option.

The button will appear above the variables then.
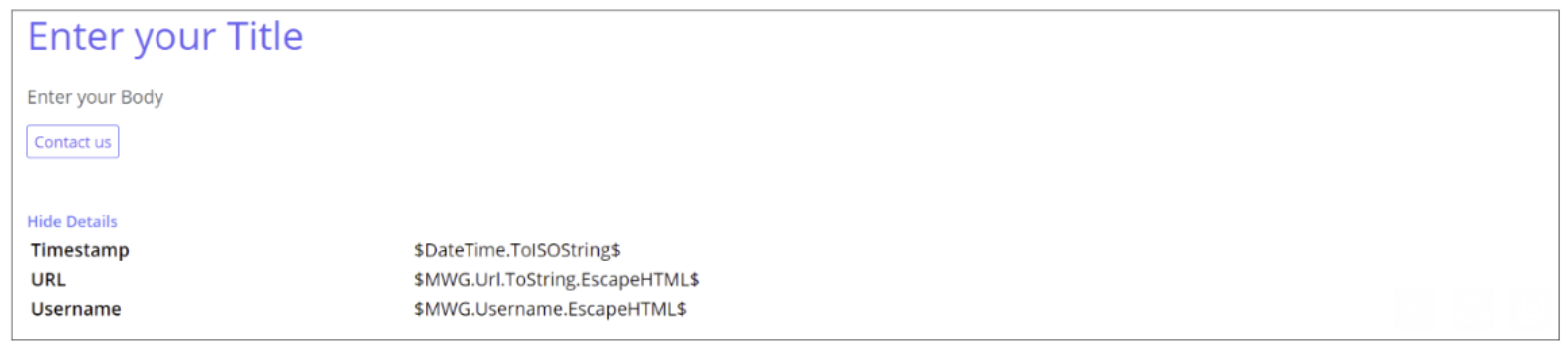
More Variables for Configuring a Template 
More variables have been added to the list you can choose from when configuring a template for an End User Notification Page.
When this page is sent to a user's browser, the values shown are related to the rule action that caused the page to be sent.
For example, when an End User Notification Page is sent to inform the user that a request for web access was blocked by a rule, the page can include a timestamp, the URL of the website that access was requested to, and the name of the user who requested access.
You can configure a template on the End User Notification Pages page. To configure variables, you work with the Variables element of a template. There are recommended variables and additional variables, which you can add as needed.

The following variables have been added to the list of additional variables.
-
URL Reputation String
-
Useragent
Skyhigh Private Access
Source IP Anchoring 
You can enable access to private and public applications using public IP addresses by defining them as Private Access applications. When you do so, all requests are routed through the Secure App Connector, ensuring traffic exits from your network and egresses with the public IPs, allowing full control and monitoring. For details, see Source IP Anchoring
.png?revision=1)
Support for non-standard http/s ports on iOS client 
Non-standard or custom ports for HTTP and HTTPS are now extended to the iOS client in addition to traffic coming from web and mobile platforms. For details, see Access Private Applications from iOS Device.
Skyhigh CASB
ServiceNow Washington DC Q2 2024 Support 
Skyhigh CASB now supports ServiceNow Washington DC Q2 2024. For details, see Supported Versions of Structured Apps.

Monthly Email Notifications for the Top Used Sanctioned Services 
The Skyhigh CASB now supports monthly email notifications named SaaS Security Coverage Monthly Report, listing the top-used sanctioned services for which granular security controls are not enabled. The email notifications assist you with securing the sanctioned services via API integration.
Integrating APIs for sanctioned services allows you to apply granular security controls to unsecured sanctioned services, secure your corporate data from exfiltration, and ensure compliance.
The email includes the following information:
- The top 10 sanctioned services for which the granular security controls are not enabled. The list is sorted based on the highest number of users for each service.
- A CSV file with a complete list of available services, including API-enabled and services without API integration.
You can enable API integration or edit the notification settings via the SaaS Security Coverage Monthly Report. For details, see Enable API Integration via Email Notifications.

Skyhigh CASB for Mural 
Skyhigh CASB for Mural allows Security Operations Center (SOC) admins to monitor user activity across various resources such as workspaces, rooms, folders, and more in Mural. For details, see About CASB Connect for Mural.

Resolved and Known Issues
 Click here to view Resolved and Known Issues
Click here to view Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.
