Skyhigh Security Cloud 6.8.1 Release Notes (Apr 2025)
Legends Used
|
General Availability |
IMPORTANT: The Skyhigh Security Cloud 6.8.1 release addresses significant library updates for enhancing security and stability. For additional information about these fixes and updates, contact Skyhigh Support.
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention(DLP)
Display and Filter for Classifications on Policy Incidents 
The Policy Incident page is updated to review policy violations from specific classifications across Sanctioned and Shadow/Web applications. These enhancements allow SOC administrators to gain valuable insights into granular Classification details for each triggered incident, enabling more effective analysis and response for a streamlined incident management process.
You can perform the following Classification-related activities on the Policy Incidents page:
- Classification Column. You can add a Classification attribute to display on the Policy Incidents table. The Classification column enables a quick and easy view of one or more triggered classifications associated with a specific incident. To add a required column to the table, see Edit Table Columns.
- Classification-based Filter. The Classification-based filter displays a list of various classification names along with the number of incidents linked to each classification. You can select different classifications to filter the incidents accordingly. This capability allows for the quick identification of classifications that have the highest incident counts. It offers valuable insights into the data that is causing the most classifications, helping the administrator in identifying potential risk areas within the organization. For details, see Policy Incidents page.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Policy Incidents page, go to Incidents > Policy Incidents

- Omnibar Search. You can use the Omnibar to search for Classifications, where predictive search suggests relevant classifications, streamlining the search process. This enhancement is particularly beneficial for incidents with multiple classifications, allowing you to quickly locate the required information. To learn more about Omnibar search, see About the Omnibar.
- ▶ Explore User Interface
-

- Dashboard Cards. You can create dashboard cards for Classifications directly from the Policy Incidents page by filtering for the specific classification you want to display on the Dashboards page. These cards provide a high-level overview of classification insights and trends, allowing you to visualize data more effectively and make informed decisions. For details, see Policy Incidents page.
- ▶ Explore User Interface
-

- Classification-based Metrics and Graphs. You can create classification-based metrics and visualize them in a graph, which provides visibility into the type of sensitive data stored in cloud services. Use the Chart View to generate classification-based metrics and graphs. For details, see Chart View.
- ▶ Explore User Interface
-

Enhanced Visibility for Sanctioned DLP Incidents 
Skyhigh now provides a focused view and a default view for easy and quick visibility into all relevant sanctioned DLP policy incidents within your organization.
Enable Focused View to Review New and Opened Incidents
Select the Focused View on the Policy Incidents page to automatically apply predefined filters that display only the incidents with the statuses of New, Opened, and Machine Learning Status (Unassigned). For details, see Focused View for Policy Incidents.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Focused View, go to Incidents > Policy Incidents > Views

Set Default View to Review Preferred Incidents
The default view allows you to display your preferred sanctioned DLP policy incidents on the Policy Incidents page. The Default View allows Security Operations Center (SOC) administrators to gain actionable insights into specific policy incidents and conduct further forensics, and allows efficient monitoring and management of policy violations. It also enhances user experience, data protection strategy, and streamlines incident management operations.
You can set a default view for the Policy Incidents page in two ways:
-
Policy Settings. Select the default view options as Focused View, Skyhigh recommended view, or Last used view. (OR)
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Default View options, go to Policy > Policy Settings > Incident Management > Select Policy Incident view

-
Policy Incidents. Click Default View Settings which redirects you to the Policy Settings page, where you can choose the required default view options.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Default View Settings, go to Incidents > Policy Incidents > Views

The preferred view is displayed each time you log in and open your Policy Incidents page. For details, see Select a Default View for Policy Incidents.
Enhanced Data Detection with Named Capture Group 
You can use custom advanced patterns to search for specific text and generate incidents upon matches. To further refine this capability, utilize enhanced regular expressions to fine-tune the matching criteria, ensuring that certain text does not trigger a match. Refining the regular expression pattern enhances the accuracy of detection and reduces false positives without altering the matched text in your incident.
Additionally, you can improve your regex with the Named Capture Group to capture specific portions of a regex pattern as a matched term, enhancing unique match counts and efficacy of the resulting DLP Incident. For an example on how to refine your regular expressions with Named Capture Groups, see Create Custom Advanced Patterns using Add Regex.
- ▶ Explore Navigation Details
-
To add enhanced regex to your Custom Advanced Patterns, go to Policy > DLP Policies > Classifications > Conditions > Advanced Patterns > Select Advanced Patterns > New > Add RegEx
Additional DLP Enhancements
Enhanced Content Detection and Extraction Libraries in Classifications 
- IDM Classifications include upgraded content detection for PowerPoints.
- The extraction library has been upgraded to increase the security and stability in Classifications.
NOTE: To utilize the above enhancements, you must download and install the latest DLP Integrator software (v.6.8.1 or later) and use the IDM train tool. For details, see Download the DLP Integrator.
-
Changed extraction logic for Documents in Classifications. Previously, the extracted text could include tracked changes (including deleted text), potentially resulting in missed detections. This issue has been resolved; extracted text now excludes track changes.
Enhanced User Experience for Classification Rule Builder 
The new Classification Rule Builder enhances the visual representation of classification rules by presenting conditions and values in a more organized and distinct format. This redesign makes identifying and adjusting specific components easier, allowing you to create and modify classification rules effectively. With its intuitive design and enhanced visual features, you can effortlessly create and manage classification rules. To view the enhanced classification rule builder screens, see the Classifications guide.
- ▶ Explore Navigation Details and User Interface
Navigation Path: To access the Classification Rule Builder, go to Policy > DLP Policy > Classifications > Create Classification > Conditions
Enhanced Incident Reporting Time on Policy Incidents 
The Policy Incident creation time is now based on the time Skyhigh Security Service Edge processed the file and applied your configured policies, providing greater clarity and accuracy in identifying potential processing lags. This replaces the original event time from the Cloud Service Provider (CSP), which could be misleading and confusing due to CSP rate-limiting delays. The original CSP event time will still be recorded and displayed in an additional column (i.e., Incident Created On, Incident Updated On, Item Modified On) on the Policy Incidents Cloud Card. Incident creation time now aligns with item modification or creation time, but it may vary slightly due to processing delays.
Enhanced File Size Limits for Shadow/Web DLP Evidence 
Skyhigh has increased the maximum limit for Shadow/Web DLP evidence files from 150 MB to 250 MB. You can now save and download larger evidence files for Shadow/Web DLP incidents using the Shadow/Web DLP Policy Incident Cloud Card or API. This enhancement allows for comprehensive analysis of significant policy violations, facilitating in-depth investigations, and effective remediation of security incidents. For details, see Save Shadow/Web DLP Evidence and Match Highlights.
Skyhigh SSE Products
Skyhigh Secure Web Gateway
Leverage Rule Tracing for Policy Insights 
Rule tracing helps the administrators identify the policies assessed to determine whether to allow or block a request from an end user. This entire process involves 3 simple steps.
- The administrator initiates a unique URL using the user name and smartmatch filter parameters, which they share with the end user.
- The end user enters that URL in the browser.
- The administrator initiates the trace and views the rules evaluated for end user-generated traffic in the SSE console.
Using this feature, you can understand the reason an end-user request was allowed or denied. For details, see Work with Rule Traces.
- ▶ Explore Navigation Details and User Interface
Navigation Path: To access the Rule Tracing page, go to Infrastructure > Web Gateway Setup > Rule Tracing
Visibility and Troubleshooting Enhancements for IPSec Tunnels 
Skyhigh now offers the ability to monitor the real-time status of your IPSec tunnels, troubleshoot on the go, update configurations as needed, and view details about source subnets.
You can also access error logs for failed or inactive tunnels and troubleshoot with enhanced error codes while establishing an IPSec connection between Skyhigh SSE and third-party devices. Enhanced error logging and a comprehensive troubleshooting guide help you identify and resolve tunnel issues more effectively. You can compare tunnel attributes to aid in diagnosing problems and re-establishing connectivity. Contact Skyhigh Support for more information.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To View Connectivity Status, go to Analytics > Connectivity

Remote Browser Isolation
Customize Browser Isolation Indicator 
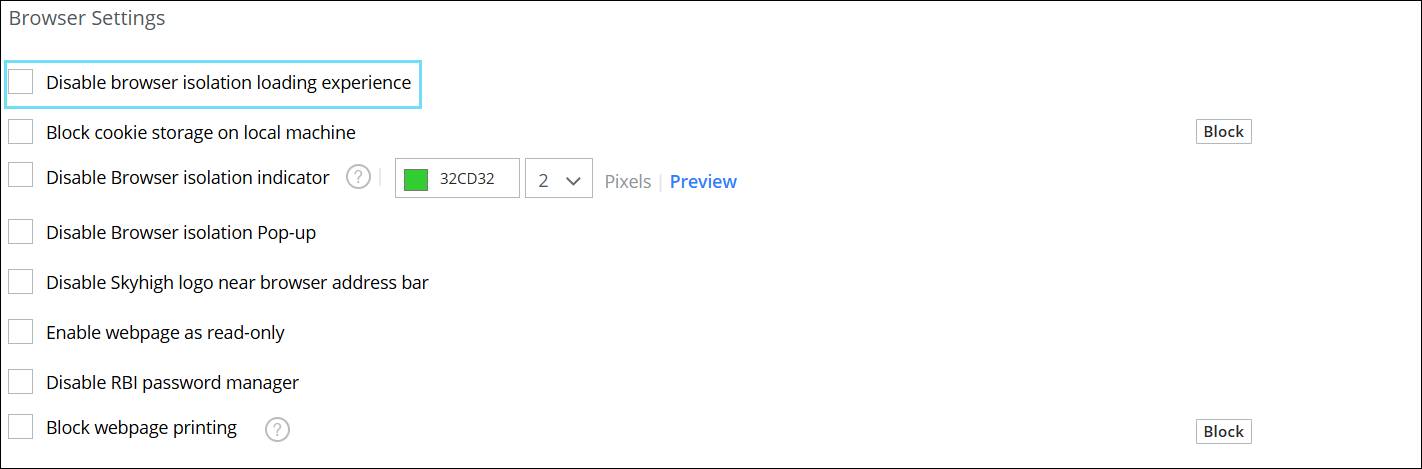
The Browser isolation indicator now features a colored indicator around a webpage, which appears when full browser isolation or risky web protection is active. You can customize the indicator by selecting the color and width of the border, with a maximum width of 5 pixels. Additionally, you can preview the browser session with your selected border color and width. For details, see Full Isolation — Use Browser Isolation for Websites Based on Your Own Selection.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Disable Browser isolation indicator checkbox, go to Policy > Web Policy > Policy > Browser Isolation > Full Isolation > Browser Settings

Disable Webpage Loading Experience in Browser Isolation 
The loading experience appears while a webpage is loading, displaying the message: Your webpage will load shortly. You can now turn off the loading message using the Disable browser isolation loading experience option. Instead, an indefinite loading bar appears at the top, which will keep you informed about the loading status of the webpage. For details, see Full Isolation — Use Browser Isolation for Websites Based on Your Own Selection.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To access the Disable browser isolation loading experience checkbox, go to Policy > Web Policy > Policy > Browser Isolation > Full Isolation > Browser Settings
Skyhigh Private Access
Deploy Secure App Connector V2 using Docker Image 
Skyhigh Private Access offers multiple deployment methods, including AMI for AWS VPCs, Azure Image for Microsoft Azure VMs, and OVA for ESXi/vSphere. You can now deploy secure app connectors for Docker on various supported platforms. Docker is a lightweight solution that effectively manages network communications for Private Applications. For details, see Deploy Secure App Connector V2 for Docker
Enhanced Private Application Discovery 
Application Discovery helps in discovering, identifying, and mapping the private applications in an organization’s network to control user accessibility. With these enhanced capabilities, the process of discovering and adding private apps has been simplified. The Discovered Apps module has been configured to allow seamless addition of discovered applications to the Private Apps list in the Private Access Configuration (PAC). For details, see Enhanced Private Application Discovery
- ▶ Explore Navigation Details
-
Navigation Path: To access the Application Discovery, go to Settings > Infrastructure > Private Access Configuration.
1_(1).png?revision=1)
Skyhigh CASB
Secure Zoom Access with Custom Granular OAuth Application 
You can now integrate Skyhigh CASB with Zoom using Zoom Granular Custom OAuth. This integration aligns with Zoom's latest version, which introduces granular scopes for custom OAuth applications. These new granular scopes provide insight into the requested data, following the principle of least privilege. For details, see Custom Granular OAuth Application for Zoom.
- ▶ Explore Navigation Details
-
Navigation Path: To integrate Skyhigh CASB with Zoom using Zoom Granular Custom OAuth, go to Settings > Service Management.
Enhanced User Activity Logging Information for Microsoft Teams 
Skyhigh enhanced the reporting of Microsoft Teams activity by adding team names, channel names, member-specific details, and communication types. This enhancement provides more specific logging information related to user activity across teams, channels, and group chats. For details, see Activity Monitoring for Microsoft Teams.
- ▶ Explore Navigation Details
-
Navigation Path: To monitor user activities in Microsoft Teams, go to Incidents > User Activity > Activities.
Support for Salesforce Spring 2025 
Skyhigh CASB now supports the latest Salesforce Spring 2025 version. For details, see Supported Versions of Structured Apps.

Support for ServiceNow Yokohama Q2 2025 
Skyhigh CASB now supports ServiceNow Yokohama Q2 2025. For details, see Supported Versions of Structured Apps.

Categorize Logs using Tags 
Use Skyhigh CASB Tag Configuration to classify and manage traffic and content across Sanctioned, Shadow, and Web services through metadata labels, or tags. These tags organize logs according to various security requirements, ensuring that relevant data is easily identifiable and actionable.
Categorize logs by:
- Geography. Distinguish logs from users in different geographies to enforce regional compliance rules, such as the GDPR for European users.
- Active Directory Attributes. Categorize logs by department (e.g., Engineering, HR) to apply appropriate web access policies.
- Security Status. Label logs linked to malware activity or policy violations for quicker threat response by building policy enforcement around it.
For details, see Tag Configuration.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To create tags, go to Settings > Infrastructure > Tag Configuration.

You can apply tags in Data Jurisdictions to enforce access restrictions and enforce DLP policies in SWG Cloud. This allows SOC teams to efficiently manage, apply policies, and analyze data at scale. For details, see Apply Web Policies to a Tag.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To apply Web policies to a tag, go to Policy > Web Policy > Policy.

Integrate Skyhigh CASB with OpenAI ChatGPT Enterprise 
Integrating Skyhigh CASB with OpenAI ChatGPT allows SOC admins to monitor and control user interactions, preventing data leaks and ensuring compliance with data privacy regulations, particularly in enterprise environments. This integration allows organizations to monitor risky user activities, maintain control over sensitive data, and safely utilize ChatGPT. For details, see About Skyhigh CASB for ChatGPT Enterprise.
- ▶ Explore Navigation Details and User Interface
-
Navigation Path: To integrate Skyhigh CASB with ChatGPT, go to Settings > Service Management.

Resolved and Known Issues
 Click here to view Resolved and Known Issues
Click here to view Resolved and Known Issues- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.
View Help Content in your Preferred Language
 Click here to learn how to change your language
Click here to learn how to change your language-
You can use the Select Language option to select a language and view the help content in that language.