Skyhigh Security Cloud 6.7.2 Release Notes (Oct 2024)
Legends Used
|
General Availability |
Skyhigh Cloud Platform
Skyhigh Data Loss Prevention (DLP)
Enhanced Proximity Condition in Classifications 
- The proximity condition in the Classification editor (found under DLP Policies > Classifications > Create/Edit Classification > Conditions > Select Criteria > Proximity) now includes a new option named Match Criteria Settings.

- Use the Match Criteria Settings option to configure the settings and view an example of the match criteria for your proximity rule.
- Select Match Criteria. Enables you to define the settings for the match criteria to trigger unique and non-unique proximity matches.

- Example of Match Criteria. Displays a real-time example of proximity matches, updated based on the settings selected in the Select Match Criteria cloud card. For details, see Create a Classification using Proximity.

- Select Match Criteria. Enables you to define the settings for the match criteria to trigger unique and non-unique proximity matches.
Security Operations Center (SOC) administrators can leverage this setting to control how match strings are paired between the criteria of the proximity rule for unique or non-unique proximity matches. It enables them to define proximity classifications with flexible match criteria, including keyword validation. Organizations can use the improved proximity condition to migrate their DLP policies with proximity conditions from data identifiers to classifications quickly and easily. It also helps to increase confidence, reduce false positives, and enhance operational efficiency in data classification.
View Classification and Sanctioned DLP Policy Events in the Audit Log 
- The Audit Log page (found under Settings > Audit Log) now provides visibility into DLP events for classifications (advanced pattern, dictionary) and sanctioned DLP policies.
- Use the DLP Classifications and CASB DLP Policy event categories to track DLP events, such as the creation, modification, and deletion of advanced patterns, dictionaries, and sanctioned DLP policies by admins within your organization.
- View details about the DLP events for advanced patterns, dictionaries, and sanctioned DLP policies based on the selected event type:
- DLP Classification Events
- Classification Advanced Pattern created
- Classification Advanced Pattern deleted
- Classification Advanced Pattern updated
- Classification Dictionary created
- Classification Dictionary deleted
- Classification Dictionary updated

- Sanctioned DLP Policy Events
- Assigned jurisdiction to CASB DLP Policy
- CASB DLP Policy Rule or Exception Group updated
- CASB DLP Policy activated
- CASB DLP Policy created
- CASB DLP Policy de-activated
- CASB DLP Policy deleted
- CASB DLP Policy exported
- CASB DLP Policy updated
- DLP Dictionary created
- DLP Dictionary deleted
- DLP Dictionary updated

- DLP Classification Events
Security Operations Center (SOC) analysts can gain insights into the DLP events for advanced patterns, dictionaries, and sanctioned DLP policies to identify and track changes in classifications and sanctioned DLP policies that impact their DLP policies. It helps SOC administrators detect and investigate any unauthorized or malicious activity related to classification and policy management. These capabilities enable SOC admins to improve their organization's data protection strategy, reduce the risk of data exfiltration, and maintain regulatory compliance.
Additional DLP Improvements 
AI Regular Expression Generator
Skyhigh has upgraded its AI-powered regular expression (RegEx) generator for Custom Advanced Patterns. The enhanced AI RegEx generator now features an advanced AI model to handle complex queries and provide accurate responses for regular expressions. It enables you to quickly and efficiently generate regular expressions for Custom Advanced Patterns. This upgrade also improves the user experience and addresses critical issues. For details, see AI RegEx Generator for Custom Advanced Patterns.

Support for Classifications and OCR in GovCloud (FedRAMP)
Skyhigh DLP key features such as Classifications and Optical Character Recognition (OCR) are now supported on the GovCloud (FedRAMP) environment. This enhancement enables organizations to identify, classify, and protect sensitive data more efficiently, ensuring compliance with federal regulations and reducing the risk of data breaches. For details, see Classifications and OCR.
Note: To enable classifications for existing GovCloud (FedRAMP) tenants, contact Skyhigh Support.
Naming Convention for Full Web DLP Evidence File Name
Skyhigh has updated the naming convention for the full Web DLP evidence file name to accurately reflect the HTTP method used in the web request. Previously, when you downloaded the saved evidence files or match highlight files for Shadow/Web DLP policy incidents using the Retrieve Incidents API, the full evidence file name was generic (request.post.txt) at the top level, regardless of the actual HTTP method (GET, PUT, PATCH) used in the captured web request.
The enhanced naming convention for the full Web DLP evidence file name provides you with clearer context and enables you to identify specific evidence files for Shadow/Web DLP policy incidents quickly and easily during investigations.
True File Type Condition in Classifications
Skyhigh has upgraded the True File Type condition (found under Policy > DLP Policies > Classifications > Create Classification > Conditions > True File Type) in classifications. During the deployment of the SSE 6.7.2 software, the True File Types details cloud card will not display file information for Skyhigh predefined file types. However, this issue does not impact the underlying scanning functionality of the DLP engine. The display issue will be resolved after the global deployment of the SSE 6.7.2 software is completed. For details on the True File Type condition, see Create a Classification using True File Type.
ML Auto Classifiers 
- The Classifications page (found under Policy > DLP Policies > Classifications > Create Classification > Conditions > ML Auto Classifier) now includes ML Auto Classifiers to automatically detect and classify various types of sensitive files in sanctioned and shadow/web services.

- It displays the matches triggered by various ML Auto Classifiers and their confidence percentage on the Sanctioned DLP Policy Incident Cloud Card.

- ML Auto Classifiers simplify the process of identifying and categorizing sensitive data by providing the following benefits. For details, see ML Auto Classifiers.
| ML Auto Classifier Benefits |
|---|
| AI-ML Powered Automatic Data Classification. Automatically classifies files with sensitive data such as PII, financial records, healthcare records, and intellectual property using AI and ML models. |
| Comprehensive Categorization. Utilizes AI and ML to automatically categorize data across all exfiltration vectors, enhancing data governance. |
| Robust Policy Framework. Leverages the categories and subcategories for ML Auto Classifiers within the policy framework to build robust DLP policies. |
| Simplified DLP Administration. Streamlines DLP management by eliminating the need for manual data classification. |
| Enhanced Operational Efficiency. Significantly boosts operational efficiency in incident management. |
| Scalability. Provides flexible scalability to support large data volumes across standard file formats. |
| Confidence. Offers clear insights into the confidence percentage in data classification, reducing the risk of data breaches. |
| Risk Reduction. Minimize the risk of inaccurate matches, preventing false positives/negatives. |
Enhanced Visibility for Sanctioned DLP Incidents 
Skyhigh now provides a focused view and a preferred view for easy and quick visibility into all relevant sanctioned DLP policy incidents within your organization.
Focused View
- The Policy Incidents page (found under Incidents > Policy Incidents > Views > Focused View) now includes a Focused View for sanctioned DLP policy incidents.

- It automatically displays incidents based on predefined filters such as incident status (new, opened).

- The focused view simplifies the task of viewing all the critical incidents by providing the following benefits. For details, see Focused View for Policy Incidents.
| Focused View Benefits | |
|---|---|
| Automatic Incident Prioritization. Automatically highlights high-priority incidents that can be potential threats or anomalies. | |
| Rapid Incident Response. Quicker response time for vulnerable incidents, such as the latest and unresolved incidents. | |
| Reduced Noise. Minimizes the volume of irrelevant incidents, such as old and resolved incidents in the incident list. | |
| Actionable Insights. Provides actionable insights to accelerate the incident remediation process, such as blocking access, quarantining files, or notifying users. | |
| Enhanced User Experience. Set the focused view as your preferred view for the Policy Incidents page. | |
| Trends and Analytics. Includes visualizations of priority DLP incidents to monitor trends or patterns in policy breaches over time. | |
| Streamlined DLP Administration. Streamlines DLP management by reducing fatigue, investigation time, and costs in SOC operations. | |
| Compliance Adherence. Ensures compliance with data privacy regulations and industry standards. |
Default View
Skyhigh now provides the flexibility to select a default view. You can select a default view for sanctioned DLP policy incidents via the Policy Settings (found under Policy > Policy Settings > Incident Management > Select Policy Incident view) or the Policy Incidents (found under Incidents > Policy Incidents > Views > Default View Settings) page. The default view enables you to display the preferred sanctioned DLP policy incidents on the Policy Incidents page. You can set the focused view, Skyhigh recommended view, or last used view as your default view for the Policy Settings page. For details, see Select a Default View for Policy Incidents.
Security Operations Center (SOC) administrators can leverage the default view to gain actionable insights into specific policy incidents and perform additional forensics on the generated incidents. It allows SOC admins to monitor and manage policy violations efficiently. Organizations can use the default view to enhance user experience, improve their data protection strategy, and streamline operational efficiency in incident management.

Skyhigh SSE Products
Skyhigh Secure Web Gateway
End User Notification Page - Coaching Page Support 
The Coaching page deployment now supports templates created through the End User Notification page feature. You can apply templates designed with the End User Notification page feature to the Coaching page. Additionally, templates customized via the UI template builder on the End User Notification page can be utilized while working with the Coaching page. To configure the coaching page, clone the coaching activation template from the Skyhigh Default tab and make modifications as required. For more details, see End User Notification Page - Coaching Page Support.

Support for Custom Trusted Certificate 
Skyhigh Web Gateway previously used a self-signed certificate from Skyhigh to block messages on sites in the SSL Bypass List. Still, it will now use a certificate from a customer-configured HTTPS Connection feature for these messages. This change addresses issues such as certificate errors encountered with websites that fail to recognize the Skyhigh-signed certificates. For SSL decryption, you now need to select the HTTPS Connection feature configuration, specifically Customer_CA in this case. For more details, see Support for Custom Trusted Certificate.
Review Changes before publish - Iterative Enhancements 
This installment of iterative enhancements offers comprehensive visibility into user modifications. Instead of a generic Modified label, you now get detailed views of all changes, including additions, deletions, and modifications. For more details, see Review Changes before publish - Iterative Enhancements.

Detailed Insights via Expandable Side Panel 
Skyhigh Web Gateway supports a side panel for Web Users, Web Traffic, Web Malware, and Isolated Site pages. Click on a row to open a side panel displaying details for all fields, including events, traffic, and usage trends. The panel is expandable and collapsible, ensuring a user-friendly experience even with many fields. For more details, see Detailed Insights via Expandable Side Panel.

Progress Bar and Ruleset Reference Checks 
Skyhigh Web Gateway includes a progress bar for deleting lists and feature configurations. When deleting a list, the system checks for references in rulesets to prevent disruptions in policy execution. The progress bar shows the status while the system searches for these references. A list can only be deleted if it is not referenced in any ruleset. For more details, see Progress Bar and Ruleset Reference Checks.

Rule Trace Enhancements 
Rule tracing facilitates the tracking of the path taken when evaluating a policy for a user, as well as the rule or ruleset that was assessed to determine whether to allow or block a request. You can obtain the logs through rule tracing and view the path that the traffic traversed in the web policy tree. You can then use the rule tracing logs for troubleshooting. The Rule Tracing page now displays details including Username, Smartmatch Filter, Region, Session ID, and Timestamp. Contact Skyhigh Support for more information.

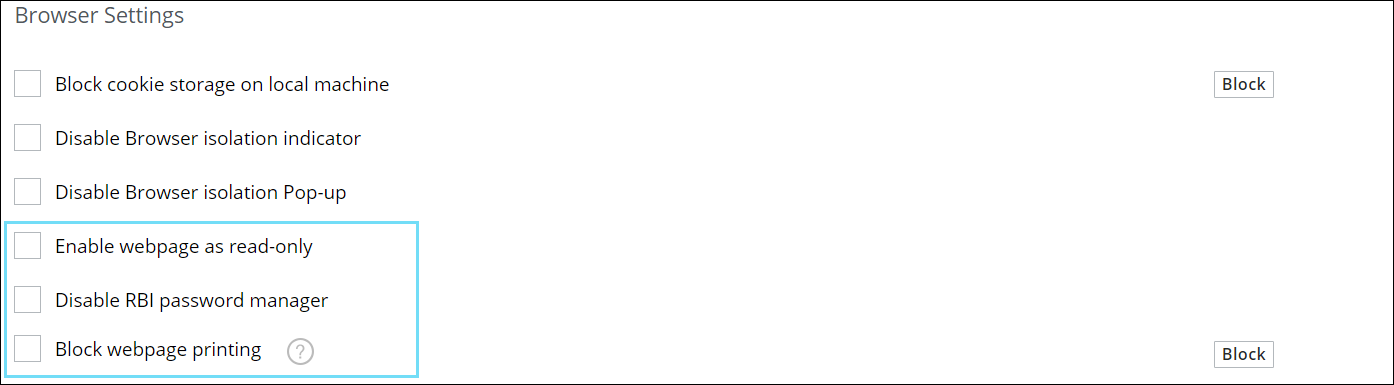
Remote Browser Isolation
Control Parameters in Policy UI for Streamlined Policy Management 
RBI capabilities previously available only through policy code are now included in the policy UI. New options allow administrators to enable read-only websites, disable the RBI password manager for login sites, and block web page printing. These features provide administrative control ensuring threat protection during full and remote isolated sessions. For more details, see Control Parameters in Policy UI for Streamlined Policy Management.
Skyhigh Private Access
Secure App Connector V2 Stickiness 
In a scenario with multiple connectors in a group, enabling this UI toggle ensures that traffic is routed through a randomly selected connector, maintaining consistent user session routing. For more details see, Add Applications.
_1_(1).png?revision=1&size=bestfit&width=1056&height=461)
Extending Network Level Access to Support UDP-Based Applications 
Private Access now extends support to relevant use cases fulfilled by traditional VPNs using Network Level Access (NLA) by securely opening the network like a VPN but based on zero trust principles for UDP-based applications. NLA supports network types such as subnet, IP, and domain wildcards in addition to domains, enabling easy migration from legacy VPNs. For more details see, Add Applications.
_12_(1).png?revision=1&size=bestfit&width=1072&height=468)
Skyhigh CASB
New Artificial Intelligence Risk Tab on the Cloud Registry 
A new Artificial Intelligence risk tab is introduced in the Cloud Registry to capture AI-related risks of a cloud service. All the LLM risk attributes are now captured under the Artificial Intelligence risk tab. For details, see the LLM Risk Attributes for AI Category Services.

Skyhigh Domain Unification to Support Chrome/Edge Browsers 
Skyhigh Security unified different domains operating under the Skyhigh console (Dashboard) to a single domain, named skyhigh.cloud to mitigate the ability of websites to misuse the cross-site tracking. Implementing this change will seamlessly enhance the user experience with the product on the Chrome/Edge browser.
After unifying to a single domain, when you use the Skyhigh console, you will be directed to the domains under skyhigh.cloud instead of myshn.net or myshn.eu. Now, all the components in the Skyhigh console work under a single domain, the skyhigh.cloud.
To know more information on domain unification, see Skyhigh Domain Unification to Support Chrome/Edge Browsers.
NOTE: Currently, no action is needed from your end. Stay tuned for more details on the scheduled date and the required actions.
Resolved and Known Issues
Click here to view Resolved and Known Issues
- For details, see Skyhigh Security Cloud Bug Fixes and Known Issues.
View Help Content in your Preferred Language
Click here to learn how to change your language
-
You can use the Select Language option to select a language and view the help content in that language.
.png?revision=1)
