Troubleshoot Common Issues
This guide helps you quickly identify and fix common Skyhigh Private Access issues across connectors, clients, policies, and SAML authentication, so you can restore secure access to private applications with minimal disruption.
Connector Issues
| Challenge | Workaround |
|---|---|
|
Secure App Connector Page – Status: Unreachable
|
Cause: TCP and UDP connectors’ tunnels are down.
|
| Secure App Connector Page – Status: Critical |
Cause: TCP or UDP connection among PA connectors is down.
|
|
CLI Tunnel Status Symptom:
|
Cause. The connection between the Connector and the PA-Gateway (PoP) is broken. Workaround.
|
Pods in InvalidImageName status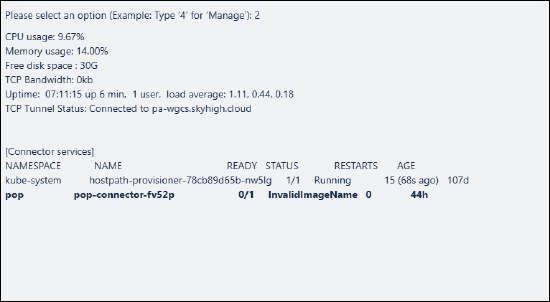 |
Cause: Intermittent network connectivity prevents pod initialization. Workaround:
|
| Pods in Unknown status Description: MountVolume.Setup fails for volume or secret cache timeout.  |
Cause: VM host is down for >24 hours, causing ECR token expiry. Workaround: Deploy the connector on a fresh VM host. |
| Installation Failures (IAM not reachable, wrong DNS, invalid proxy, duplicate configs) | Cause: Connector deployment script received invalid data or failed to reach required endpoints. Workaround:
|
Client Issues
| Challenge | Workaround |
|---|---|
SCP Window Shows PA Status: Not Connected 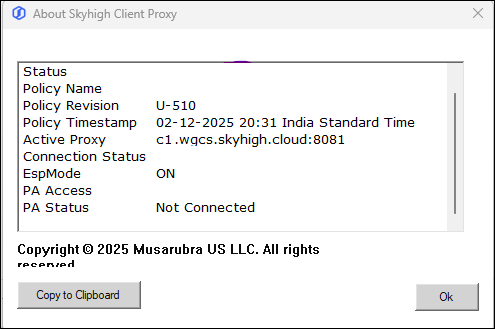 |
Cause: The client cannot establish outbound connectivity to the Skyhigh proxy service on the required ports (typically 8080 or 443).
NOTE: In SCP 5.x, the client intercepts traffic locally, so telnet and packet capture tools may not show any results.
|
This Site Can’t Be Reached When Accessing a Private Application |
Cause: The application is not configured as a Private Application in the SSE UI.
|
Host Not Resolvable 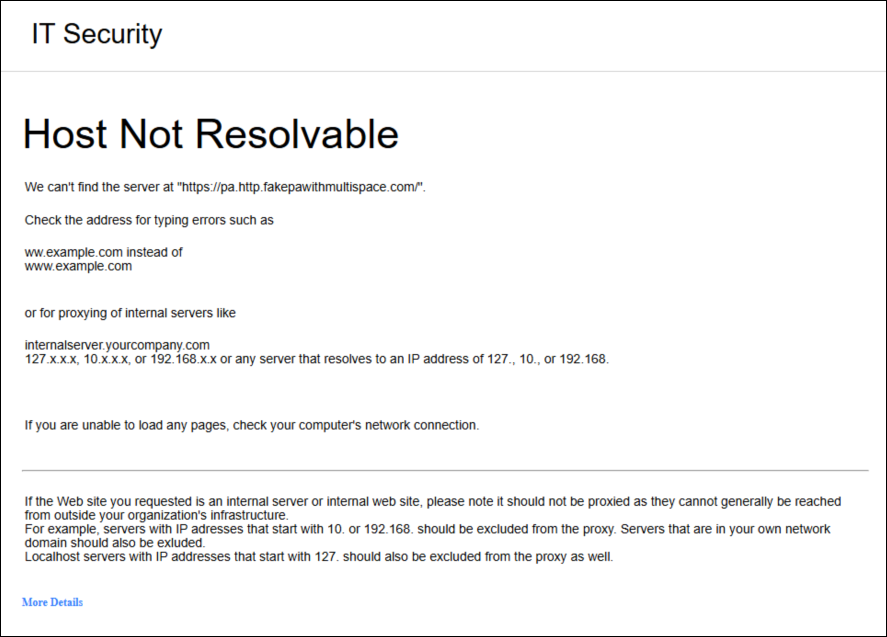 |
Cause: The Private Application is not configured or DNS resolution fails.
|
No Route Found to This Private Application |
Cause:
Workaround:
|
Cannot Access Private Application – Not Resolvable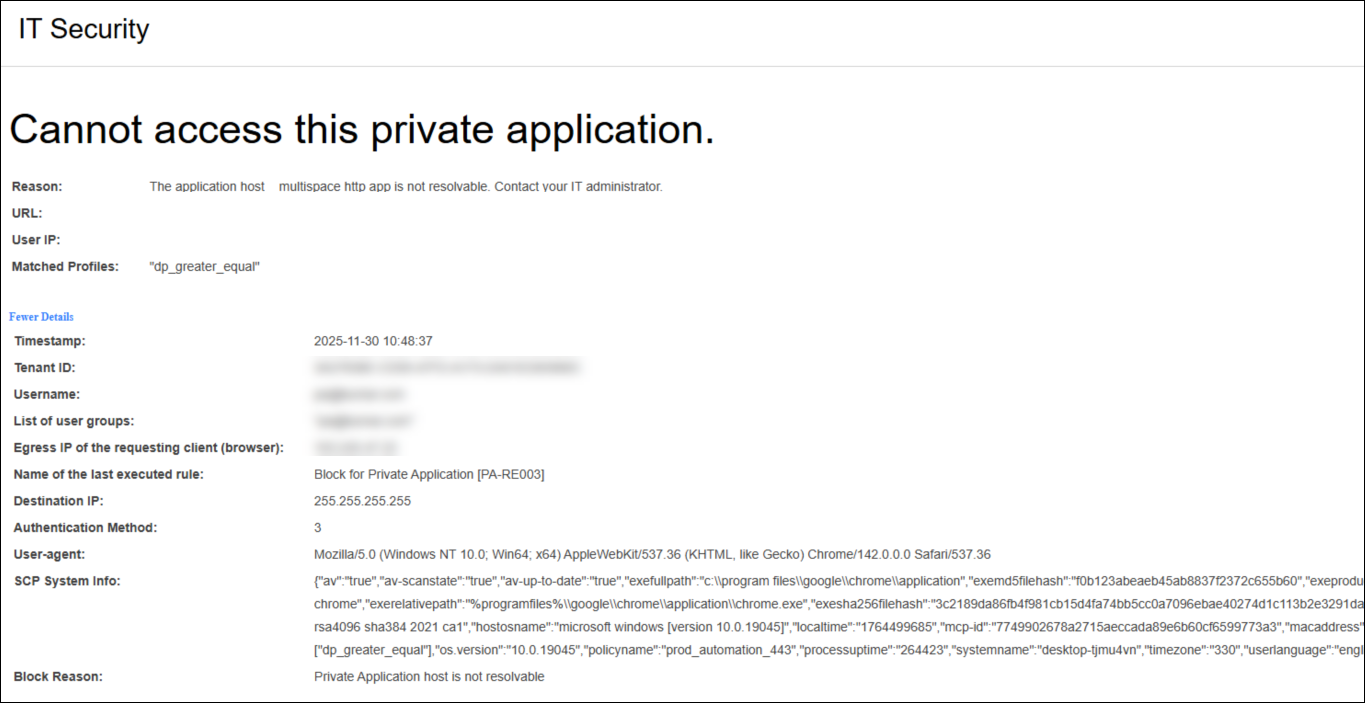 |
Cause: The connector cannot resolve the Private Application.
|
|
Cannot Access Private Application – Not Reachable Failure Description: The connector resolves the host to an IP address, but the IP or port is unreachable. |
Cause: The connector cannot reach the Private Application endpoint.
|
Bad Gateway – Proxy Did Not Receive a Valid Response in Time  |
Cause:
Workaround:
|
|
SSL Handshake Error – Handshake with Remote Server Failed Failure Description: Connection refused from the ZTNA gateway or backend service. |
Cause: The Cloud PoP may be down or unstable.
|
|
Cannot Connect – Proxy Could Not Connect to Destination in Time Failure Description: Connection reset or cannot connect to the destination server. |
Cause:
Workaround:
|
SCP Client Tunnel Status: Failed to Connect (Phase 1 / Phase 2)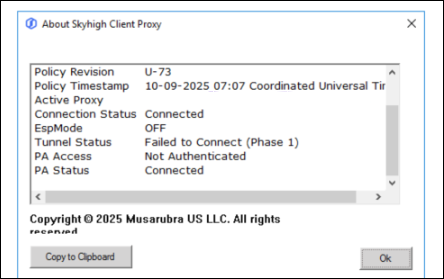 |
Cause: The client cannot reach the tunnel endpoint to establish a connection. Workaround:
|
Policy Issues
| Challenge | Workaround |
|---|---|
| Private Applications Not Shown on PA Dashboard (Web Policy Tree Empty) The PA dashboard ( https://api.wgcs.skyhigh.cloud/ztna/dashboard) is empty and does not list any Private Applications. |
Cause: The Private Access section under Policy > Web Policy tree is empty. Workaround:
|
| Private Applications Not Shown on PA Dashboard (SCP Proxy Bypass) The PA dashboard ( https://api.wgcs.skyhigh.cloud/ztna/dashboard) is empty and does not list any Private Applications. |
Cause:
Workaround:
|
|
Redirection to SAML Authentication Not Working Accessing |
Cause:
One or more of the following conditions exist:
|
| TLS Handshake Error 500 for RDP or SSH-Based Private Applications The Analytics PA Usage page shows a TLS handshake error 500 for RDP or SSH-based Private Applications. |
Cause: The connector cannot reach the Private Application. Workaround:
|
SAML Login Issues
| Challenge | Workaround |
|---|---|
| SAML Login Failure | Cause: SSE UI has misconfigured SAML attributes. Workaround:
|
| Clientless Access Loops on Email Domain Page After SAML Authentication | Cause: The SAML User ID attribute does not match the email entered on the email domain page. Workaround:
|
| Clientless Access Loops on Email Domain Page and Does Not Redirect to IdP Login | Cause: The domain configured in Web Gateway SAML settings does not match the entered email domain. Workaround:
|
| PA Dashboard Shows No Private Applications The PA dashboard (https://api.wgcs.skyhigh.cloud/ztna/dashboard) does not list any Private Applications. |
Cause:
|


