Incidents API Paths
Retrieves List of Incident.information Keys
POST /v1/queryIncidentInformationKeys
Description
For an authenticated tenant, it retrieves a list of keys to access values from the Incident.information map.
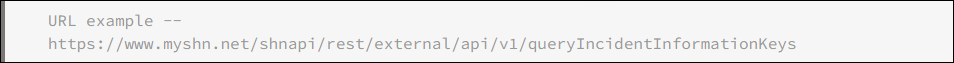
URL example — https://www.myshn.net/shnapi/rest/external/api/v1/queryIncidentInformationKeys
Responses
| HTTP Code | Description | Schema |
|---|---|---|
|
default |
List of keys with descriptions for corresponding Incident types used to access values from the Incident.information map. |
Retrieves Incidents
POST /v1/queryIncidents
Description
For an authenticated tenant, it retrieves a list of incidents in ascending time modified order.
URL example — https://www.myshn.net/shnapi/rest/external/api/v1/queryIncidents?limit=500
Payload example — { "startTime":"2016-12-15T00:00:00Z", "endTime":"2017-01-23T00:00:00Z", "actorIds":["name1@shn.net","name2@gmail.com"], "serviceNames":["Service1","Service2"], "incidentCriteria":{ "categories":[ {"incidentType":"Threat"}, {"incidentType":"Alert","category":"Policy"} ] } }
Parameters
| Type | Name | Description | Schema | Default |
|---|---|---|---|---|
|
Query |
limit |
Maximum number of items that will be returned within a single response. If value exceeds maximum 500 it will not be flagged as an error but will also not increase results. |
integer (int32) |
50 |
|
Body |
criteria |
Criteria to filter the response data with. Be sure to set required startTime as beginning time of incidents to retrieve. The criteria fields that can be used for this query are :== [ startTime | endTime | actorIds | serviceNames | incidentCriteria ] |
Responses
| HTTP Code | Description | Schema |
|---|---|---|
|
default |
Response information and an array of incidents in ascending time modified order starting at startTime within Criteria. Check responseInfo –> error for any unexpected errors or warnings. Use nextStartTime within responseInfo for the continuation of this query in next request. |
Sample Output
For a threat
{
"activityNames": [],
"actorId": "test_mitre_robot_0_1598664766_87@shn.com",
"actorIdType": "USER",
"incidentGroup": "Threat.Compromised Accounts.Land Expand Exfiltrate",
"incidentGroupId": null,
"incidentId": "THR-51938",
"incidentRiskScore": 10.0,
"incidentRiskSeverity": "high",
"information": {
"anomalyCount": 4,
"anomalyIds": "",
"category": "Compromised Accounts",
"device": {
"ip": "0.0.0.0"
},
"mitreTactic": [
"Persistence",
"Exfiltration",
"Initial Access",
"Collection"
],
"mitreTechnique": [
"Email Collection",
"Share Data from Cloud Account",
"Valid Accounts",
"Account Manipulation"
],
"userAttributes": {}
},
"instanceId": null,
"instanceName": null,
"responses": [],
"serviceNames": [
"Office365",
"Office365",
"OneDrive",
"Office365",
"AzureAD",
"Exchange Online"
],
"significantlyUpdatedAt": "2020-09-12T23:43:49.314Z",
"status": "opened",
"timeCreated": "2020-09-12T23:39:48.824Z",
"timeModified": "2020-09-12T23:43:49.314Z"
}
For a config audit incident
{
"activityNames": [],
"actorId": "N/A",
"actorIdType": "USER",
"incidentGroup": "Alert.Policy.Audit",
"incidentGroupId": null,
"incidentId": "AUD-20172",
"incidentRiskScore": 7.0,
"incidentRiskSeverity": "medium",
"information": {
"accountId": "400976400997",
"category": "SecureConfig",
"configType": "EC2",
"contentItemCreatedOn": "2020-06-20T11:42:51.805Z",
"contentItemId": "i-0e36fb006d25da6cb",
"contentItemName": "i-0e36fb006d25da6cb",
"contentItemType": "EC2",
"eventId": "57",
"mitreTactic": ["Credential Access"],
"mitreTechnique": ["Unsecured Credentials"],
"policyId": 516717,
"policyName": "EC2 instance should be configured to use Instance Metadata Service version 2 (IMDSv2)",
"scanName": "Security Configuration Audit Scan For AWS",
"scanRunDate": "2020-06-20T11:39:57.551Z",
"userAttributes": {}
},
"instanceId": 11994,
"instanceName": "Default",
"responses": ["Violation Detected"],
"serviceNames": ["Amazon EC2"],
"significantlyUpdatedAt": "2020-06-21T11:31:55.839Z",
"status": "archived",
"timeCreated": "2020-06-20T11:42:51.805Z",
"timeModified": "2020-06-21T11:31:55.841Z"
}
NOTE: If you have multiple accounts in different tenants, then use the header "bps-tenant-id" along with the corresponding BPS ID in the header section. For further assistance on Tenant ID, contact Skyhigh Security Support.
Query Incident Information Keys API
The Query Incident Information Keys API retrieves list of Incident.information keys to access values from the Incident.information map.
Responses
| Code | Description |
|---|---|
| default | List of keys with descriptions for corresponding Incident types used to access values from the Incident Information map. |
Schema
| Name | Description | Type | Example |
|---|---|---|---|
| IncidentInformationKeysByType | The list of information keys available per incident type. The information keys consist of two fields, key ::= key to access value from information map, and value ::= description of the value that will be retrieved. | String | Values :== [ AuditViolation (Alert.Audit...) | PolicyViolation (Alert.Policy.Dlp) | SanctionedAnomaly (Alert...) | ShadowAnomaly (Alert...) | Threat (Threat...) ] |
| informationKeys | A pair of key and value (standard map entry). | String |
