How the Skyhigh Security Service Edge Components Work Together
Skyhigh Security Service Edge (SSE) brings Skyhigh CASB and Skyhigh Secure Web Gateway together on a single platform to keep data and your corporate network safe.
Security Service Edge (SSE) uses a variety of technologies to manage and control the flow of traffic and access requests between your locations, network and the cloud, including proxies, filtering and secure tunnels, as shown in the following graphic.
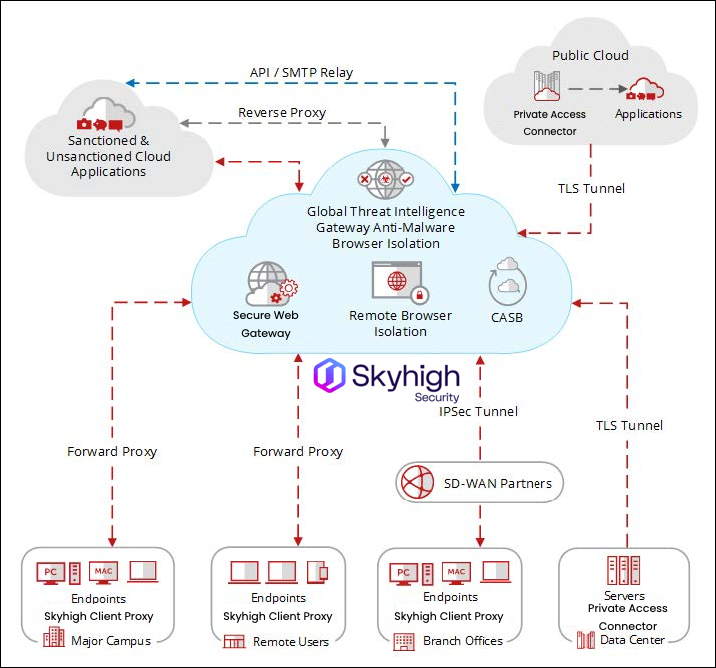
The SSE platform uses Secure Web Gateway to provide control and policy enforcement over web traffic and Shadow cloud services — those not approved for corporate use by IT departments — via forward proxy.
Secure Web Gateway also analyses the nature and intent of all content and active code entering the network via webpages to protect against malware, hidden code, or control applications.
Direct API traffic is managed by the CASB, relying on streaming activity feeds from the cloud service provider and enforcing security by making API calls back into the service.
Skyhigh Client Proxy
Client Proxy is installed on endpoints. The client software is location-aware, and detects whether users are working inside or outside the network. When users are outside the network, it directs their traffic to Secure Web Gateway for filtering.
To manage Client Proxy, you can configure the redirection policy, including bypass lists in the Skyhigh CASB user interface. Policy changes are stored in the Global Policy Store in the cloud. Secure Web Gateway accesses the GPS when requested by the Client Proxy, which then allows it to permit or block the request based on the rule set in the policy.
When the Client Proxy software redirects HTTP/HTTPS traffic, it adds metadata to the requests. Secure Web Gateway uses the metadata (for example, group membership) when applying web protection policies. When the Secure Channel option is enabled in Client Proxy, the cloud proxy server certificate is validated against the device certificate store, establishing a secure connection. Traffic can also be blocked if the validation fails.
In addition to Client Proxy, you can also forward internet-bound traffic from the corporate network to Secure Web Gateway over tunnels using either a dynamic IPsec or GRE protocol. To do so, you should have an IPsec or GRE capable device, which could establish a tunnel to Secure Web Gateway. You can choose appropriate tunneling method based on your corporate needs. For more details, see Skyhigh Client Proxy.
Skyhigh Mobile Cloud Service
Traffic from mobile users can be directed through Security Service Edge (SSE) using Skyhigh Mobile Cloud Security. When Mobile Cloud Security has been set up on the device, HTTP/HTTPS traffic is redirected to Secure Web Gateway for filtering through a VPN gateway. This is configured through the Skyhigh CASB user interface. For more details, see Skyhigh Mobile Cloud Security (SMCS).
Skyhigh Private Access
Skyhigh Private Access provisions access to private applications securely from any location and device. Using Skyhigh Private Access, you can enforce granular access policies, multilayer authentication, and continuous assessment of endpoints. For more details,see Skyhigh Private Access.
Remote Browser Isolation
When Remote Browser Isolation is enabled as Risky Web, a web session will be isolated on a remote server whenever the Skyhigh Security algorithm is not confident the session should be allowed or blocked based on the existing web policy.
When the remote browser is activated, the content is passed through the Secure Web Gateway, so the traffic has consistent policies and data loss prevention across isolated and non-isolated sessions. The content is then sent back to the isolated server and returned to the user's browser as an image, video or audio stream.
Under Full Isolation, browsing is isolated in this way by default, unless you have enabled exemptions under your web policy. For more details, see Remote Browser Isolation (RBI).
Classifications
Classifications created in the unified classification editor can be applied to both your Sanctioned and Web/Shadow data protection policies. You can also configure Skyhigh CASB to use Skyhigh Security DLP Endpoint classifications you have created in Trellix ePO, allowing you to select different classification rules for different cloud services. When a rule is triggered and a policy takes action, and incident is generated and displayed in Skyhigh CASB Policy Incidents.
Reverse Proxy
Security Service Edge (SSE) uses a reverse proxy to connect to those applications that do not have a direct API, and routes traffic from the cloud service to the CASB proxy to protect your organization’s sensitive information when it moves in and out of the cloud.
Reverse proxy is inserted into the traffic flow by modifying the SAML endpoint in the cloud application’s entry in the customer’s identity provider. When traffic is directed through the reverse proxy, it can perform functions such as conditional access control, DLP, and activity monitoring.
