Enable Real-Time DLP Scan for Files Uploaded via Browser
|
Limited Availability: To access the File Upload Pre-Scan feature, contact Skyhigh Support. |
File Upload Pre-scan is designed to detect and prevent the unauthorized transfer of sensitive information outside the organization. This capability functions as a gatekeeper at the browser level, automatically scanning files for sensitive or confidential data before they are uploaded through web applications. It is application agnostic and applies across a wide range of services, including cloud storage platforms such as Google Drive and Dropbox, and collaboration tools such as WhatsApp Web and Microsoft Copilot. Network-level inspection is handled by the Secure Web Gateway (SWG). This feature operates within the browser, allowing it to inspect content before the original application applies technologies such as end-to-end encryption or WebSockets, which might otherwise prevent the Secure Web Gateway (SWG) from analyzing the content.
How it Works?
When a file is accessed through a browser-based application, it is submitted to SWG and scanned against the organization's configured web and DLP policies.
Skyhigh Web Gateway uses the existing Web and DLP rules to identify sensitive data patterns and perform content inspection during file prescan. Files are scanned in real time before they enter the application running in the browser. During the pre-scan, the SWG inspects the content and verifies compliance with the configured policy, including all DLP and other rules.
If sensitive data is detected or a policy violation occurs, the browser application will not be permitted to access the file. When Agentless Notification is enabled, a message appears stating: The content you requested is blocked by your organization’s security policy, along with violation details. The block page is configured for the violated policy and can be customized within the appropriate ruleset.
Use Cases for File Upload Prescan in Web DLP
Use Case 1: Prevent Sensitive Data Uploaded to Web Whatsapp
A sales representative attempts to upload a file containing confidential customer data or trade secrets through WhatsApp Web, which uses end-to-end encryption. Skyhigh Web Gateway scans the file in real time using Web DLP policies. If sensitive content is detected, the upload is blocked. If Agentless Notification is enabled, the user receives a notification. The incident is logged for visibility and can be forwarded to the security team for review.
Use Case 2: Prevent Confidential Data Uploads via Copilot Web
An employee uploads source code or internal documents to Copilot Web, which typically uses WebSockets, a protocol that Secure Web Gateway (SWG) does not presently support. To address this, SWG can inspect the content during the prescan phase, scanning for embedded secrets, credentials, or proprietary information using custom DLP rules before the data is transmitted by Copilot Web. If a violation is found,Copilot will be prevented from accessing the file. With Agentless Notification enabled, the user is notified. This helps prevent accidental exposure of intellectual property to external AI services or cloud platforms.
Configure File Upload Pre-Scan for Browser
To configure File Upload Pre-Scan Ruleset in Browser Control, follow these steps:
- Go to Policy > Web Policy > Policy > New Ruleset and Select Library Rulesets.
- On the Select Library Rulesets page, under the Browser Control Rulesets, select the Agentless Notification and File Upload Pre-scan checkbox.
NOTE: It is recommended to use Agentless Notification in conjunction with File Upload Pre-Scan, allowing users to be notified when actions are blocked.
- Click Add.

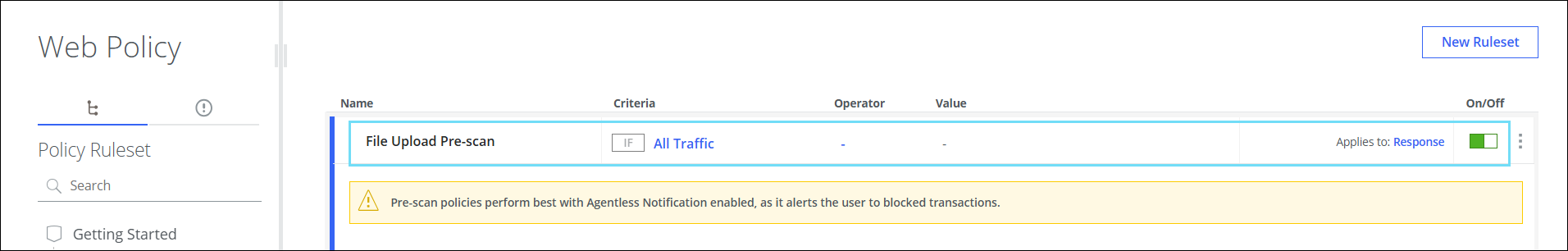
- Go to Web > Policy > Web Policy > Policy Ruleset > Browser Control > File Upload Pre-Scan.
- On the File Upload Pre-scan page, locate the File Upload Pre-scan rule and turn On the toggle to enable it.
-
Click the Yellow Badge to Save and Publish the policy changes.
File pre-scan occurs when a file is uploaded to the browser through a file selection dialog or drag-and-drop. If a file violates any configured policy rules, the browser will be blocked from accessing the file.
- If Agentless Notification is enabled, a block notification appears to inform the user.
- If Agentless Notification is disabled, no pop-up appears, but the upload is silently blocked in the background.
In both cases, the activity is recorded in the Audit Logs and DLP Incident.
Configure File Upload Pre-Scan Settings
The File Upload Pre-Scan Settings include two key components: Preset Rules and Scan Limit.
- Preset Rules. To specify which websites should be pre-scanned, admins should use the standard policy scoping criteria, particularly the All Traffic to define the scope of inspection. The exclusion list allows administrators to exclude only those sites that are already included in the scoping rule.
- Scan Limit. Configure a maximum file size threshold. Files that exceed this limit will be skipped during scanning.
To access the File Upload Pre-scan settings, go to: Web > Policy > Web Policy > Policy Rule Set > Browser Control > File Upload Pre-scan.
Configure Site Exclusion Settings
Site exclusion settings allow you to control which websites are subject to scanning and which are exempt.
Importance of File Upload Pre-scan Scoping
File Upload Pre-scan is most effective when scoped to websites known to prevent inspection. Since SWG cannot scan uploads on encrypted (WhatsApp and Facebook Messenger) or WebSocket-based platforms (Copilot Web), targeting these sites ensures the feature provides actual security value. When the policy is scoped to apply only to specific sites, using the exclusions list is typically unnecessary. Secure Web Gateway (SWG) can already scan uploads for most websites, so enabling File Upload Pre-scan for all sites provides minimal additional benefit and may introduce unnecessary overhead. This is because content is uploaded twice during the File Upload Pre-scan process:
- First upload. The file is sent to the Secure Web Gateway (SWG) for inspection before it proceeds anywhere else.
- Second upload. After inspection, the same file is uploaded again to the destination website or application (for example, WhatsApp, Facebook Messenger, or Copilot Web).
Consider the potential impact on user experience and bandwidth usage, especially for large files or metered network connections, where duplicate uploads may lead to delays or additional charges.
Optimized Policy Scoping for Uninspectable Sites
Admins should configure policy scoping to target sites that prevent inspection (WhatsApp, Facebook Messenger, Copilot Web) to ensure meaningful protection. Scoping policies this way helps prioritize protection efforts and maintain system performance.
You can exclude specific sites from File Upload Pre-Scan by configuring two settings:
-
Default Site exclusions. Predefined list provided by Skyhigh. This list shows sites that Skyhigh has identified as incompatible with File Upload Pre-Scan. Clone and edit options are unavailable on the default site exclusions list because it's a Skyhigh maintained list.

-
User-Defined Site exclusions. This list allows you to specify websites where the File Upload Pre-scan should not be applied. Use this list to disable scanning on sites where the feature may interfere with normal page behavior or functionality. Any site added to this list is excluded from File Upload Pre-scan enforcement.

Configure Scan Limit
You can control which files undergo pre-scan by defining a maximum file size limit. This helps optimize performance and avoid unnecessary processing for oversized files. To configure the file size limit, enable the Skip pre-scan if file size exceeds the specified limit option. This setting allows you to define the maximum file size eligible for pre-scan inspection. Files exceeding this limit will bypass the pre-scan process and proceed directly to the destination application without being scanned.
DLP Processing Limits
Data Loss Prevention (DLP) scanning within SWG has built-in size restrictions:
- The default limit is 50 MB.
- The Advanced DLP entitlement is up to 250 MB.
Increasing the prescan limit beyond the DLP processing limit will result in the content not being DLP scanned. To enable scanning for larger files, update the default value in the Scan Limit settings.
- To configure the scan size limit: go to Web > Policy > Web Policy > Policy Ruleset > Browser Control > File Upload Pre-scan.
- Within the File Upload Pre-Scan section, locate the Scan Limit under Preset Rules.
- You can customize the scan size limit using the menu and select a value in KB, Bytes, MB, or GB.
- Click Save to apply the configuration.
After the configuration is saved, any file uploaded via a browser that exceeds the configured scan size limit will bypass the pre-scan process. These files are not blocked and will continue to upload without inspection.

Detect Pre-scan Requests in SWG policy
The pre-scan request uses a standardized URL format: https://xxxxx/skyhigh/aaaaaa/filename, where xxxxx represents the domain of the currently loaded page in the browser, aaaaaa indicates the action being performed (typically file change or drop), and filename is the name of the file involved. This URL can also be detected in SWG policy and used to specify different policy behaviour for prescan requests, using normal policy scoping conditions.
This URL is logged in DLP incidents and audit logs for visibility and tracking.
